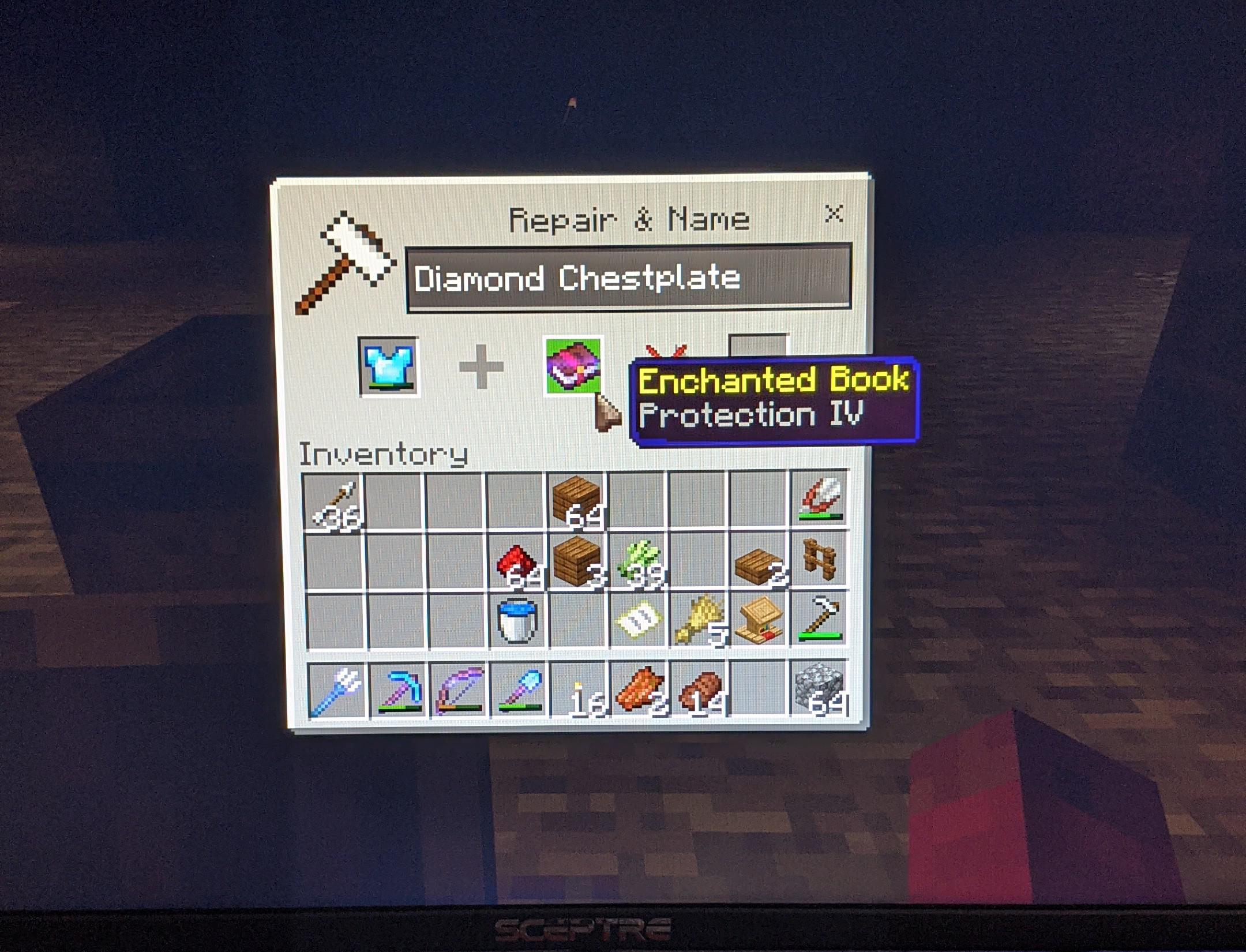
Unlocking Superior Shielding: A Deep Dive into Protection IV
Unlocking Superior Shielding: A Deep Dive into Protection IV In today’s world, the need for robust protection against various threats is paramount. Whether safeguarding sensitive data, critical infrastructure, or even personal well-being, understanding and implementing effective shielding measures is crucial. This article provides an in-depth exploration of Protection IV, a concept representing an advanced level … Read more